Document updated on Nov 23, 2021
OAuth 2.0 Client Credentials (2-legged flow)
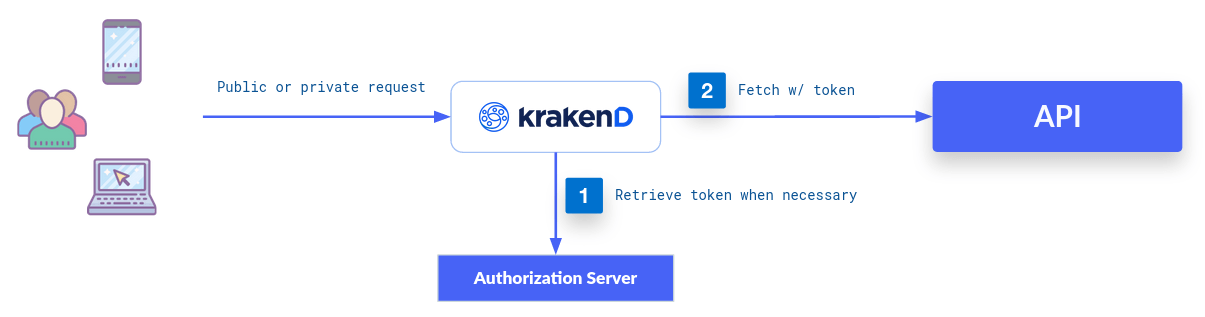
Through the OAuth 2.0 Client Credentials Grant, KrakenD can do a 2-legged OAuth2 flow, which means that the gateway requests to your authorization server an access token before reaching the backend’s protected resources. The token refreshes when needed.
The client credentials authorize KrakenD, as the client, to access the protected resources.
Successfully setting the client credentials for a backend means that KrakenD can get the protected content. Still, the endpoint offered to the end-user will be public unless you protect it with JWT or another end-user authentication mechanism.
Configuring OAuth2 Client Credentials
To access a protected resource using client-credentials, add under every backend the appropriate extra_config.
The namespace used is "auth/client-credentials". Sample configuration below:
{
"backend": [
{
"url_pattern": "/protected-resource",
"extra_config": {
"auth/client-credentials": {
"client_id": "YOUR-CLIENT-ID",
"client_secret": "YOUR-CLIENT-SECRET",
"token_url": "https://your.custom.identity.service.tld/token_endpoint",
"endpoint_params": {
"audience": ["YOUR-AUDIENCE"]
}
}
}
}
]
}client_idstring: The Client ID provided to the Auth serverclient_secretstring: The secret string provided to the Auth servertoken_urlstring: The endpoint URL where the negotiation of the token happensscopes: string,optional A comma-separated list of scopes needed, e.g.:scopeA,scopeBendpoint_paramslist, optional: Any additional parameters you want to include in the payload when requesting the token. For instance, adding theaudiencerequest parameter may denote the target API for which the token should be issued.
Auth0 integration
The following example demonstrates a complete configuration to fulfill the requirements of Auth0. It is essentially the same configuration we have shown above, but with some additions, explained after the code:
{
"endpoint": "/endpoint",
"backend": [{
"url_pattern": "/backend",
"extra_config": {
"auth/client-credentials": {
"client_id": "YOUR-CLIENT-ID",
"client_secret": "YOUR-CLIENT-SECRET",
"token_url": "https://custom.auth0.tld/token_endpoint",
"endpoint_params": {
"client_id": ["YOUR-CLIENT-ID"],
"client_secret": ["YOUR-CLIENT-SECRET"],
"audience": ["YOUR-AUDIENCE"]
}
},
"modifier/martian": {
"fifo.Group": {
"scope": ["request", "response"],
"aggregateErrors": false,
"modifiers": [
{
"header.Modifier": {
"scope": ["request"],
"name" : "Accept",
"value" : "application/json"
}
}
]
}
}
}
}]
}The code above works with Auth0. The difference with the basic example is the way both the id and the secret are passed as endpoint_params, as auth0 ignores the auth header and expects the credentials sent as JSON data or form body.
